How to Use GenAI to Fuzz and Detect Injection Vulnerabilities
Understanding how to fuzz web application parameters is a critical skill, if you're trying to hack a web application.
But if you've ever tried fuzzing using general wordlists, you’ve likely faced frustration: large wordlists take forever to run, and most tools don’t even tell you if the responses are vulnerable.
Here’s the good news:
With help of GenAI (i.e. ChatGPT), you can create smarter, smaller wordlists and build scripts to detect vulnerabilities automatically.
In the next 5 minutes, you’ll be equipped to efficiently fuzz web applications and find injection vulnerabilities like a Pro Hacker.
Let’s dive in!
Why Traditional Fuzzing is a Waste of Time?
Why General Wordlists Fail?
Most wordlists are designed to cover every possibility. This sounds great, but in practice:
They’re huge: Thousands or even millions of entries can take hours or days to run.
They’re generic: These lists don’t consider the specific context or technologies used by the target application.
Why Manual Vulnerability Detection Fails?
Tools like WFuzz, Burp Intruder and ffuf can perform fuzzing, but they simply send requests and log responses. You’re left to:
Analyze response codes, headers, and body content manually.
Guess whether an unusual response is a sign of vulnerability.
This approach is not only slow but also easy to miss critical vulnerabilities.
How GenAI-Powered Fuzzing and Detection Can Help?
What if you could:
Generate a targeted, precise wordlist?
Automatically identify vulnerabilities in the responses?
With GenAI and custom scripts, you can!
Here’s how:
Step 1: Gather Target Information
Before fuzzing, understand the application:
Technology Stack: Is it using PHP, Python, Node.js, etc.?
Frameworks: Is it built with frameworks like Laravel, Django, or Express.js?
Parameter Patterns: Identify query parameters, headers, JSON keys, and more.
Authentication: Does it require special tokens or cookies?
Step 2: Use GenAI to Generate Wordlists
Instead of relying on massive pre-built wordlists, use GenAI to craft a tailored list.
Here’s how:
Describe the Target: Provide GenAI with details such as the tech stack, known parameters, and any special syntax (e.g., SQL-like or JSON).
Request Specific Payloads: Ask for payloads specific to injection types.
Refine the List: Review and tweak the output to remove duplicates or irrelevant payloads.
Example GenAI Prompt:
You're an expert ethical hacker. The web application you're hacking uses PHP language and MySQL database. The server is Apache. You've found a POST body parameter which looks like it might be vulnerable to SQL Injection.
Write 100 non-duplicate lines of wordlist to fuzz the parameter. After fuzzing with this wordlist you should be sure whether the parameter is vulnerable.
The lines of this wordlist should be URL encoded.
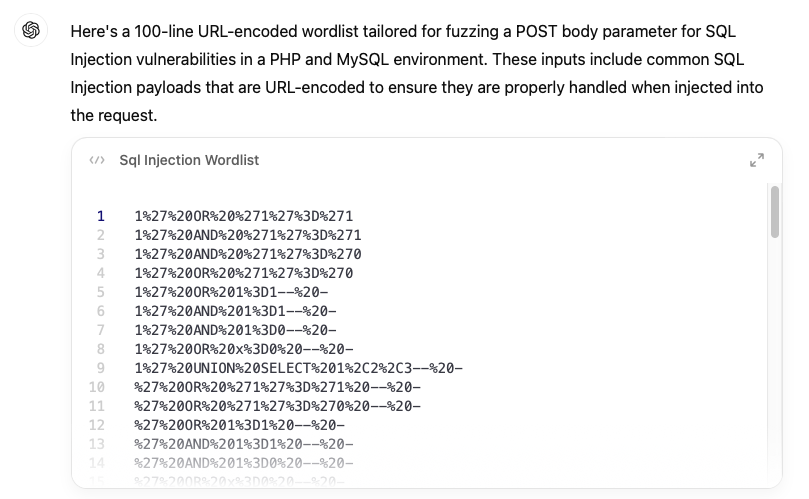
Step 3: Automate Detection with Scripts
After generating a wordlist, automate vulnerability detection with Python or any scripting language you’re comfortable with. OR you can use GenAI to generate detection script functions for you.
Sample Python Script
Here’s a simple script to fuzz parameters and detect SQL injection vulnerabilities:
import requests
# Target URL and parameter
url = "https://example.com/login"
params = {"username": "FUZZ", "password": "test"}
# Fuzz payloads
payloads = [
"' OR 1=1--",
"' UNION SELECT NULL--",
"admin' --",
]
# Fuzzing loop
for payload in payloads:
print(f"Testing payload: {payload}")
params["username"] = payload
response = requests.post(url, data=params)
# Simple detection logic tailored for the application
if "Welcome" in response.text or response.status_code == 200:
print(f"[+] Vulnerable to SQL Injection! Payload: {payload}")
else:
print("[-] Not vulnerable.")How It Works:
Replaces the
FUZZplaceholder in theusernameparameter with each payload.Sends POST requests to the target.
Checks if the response indicates a vulnerability (e.g., status code or specific text).
Expand to Other Vulnerabilities
Modify the payloads and detection logic to test for:
XSS: Check if payloads are reflected in the response.
Command Injection: Detect unusual system behavior or output.
Path Traversal: Look for directory listings or file contents.
Conclusion
Fuzzing doesn’t have to be slow or ineffective.
By using GenAI for smart wordlist generation and automating detection with scripts, you can uncover vulnerabilities efficiently and effectively.
Follow me on 𝕏 @CyberMehul for updates on new blogs.